Access
SSH from a terminal is the only allowed protocol to
log in - other insecure protocols (telnet,
rlogin, rsh, ftp, etc.)
are unsupported and disabled by default.
ssh -Y john@rama-login.research.mtu.edu
Replace john with your Michigan Tech ISO username;
supply ISO password when prompted. Note that SSH, from
off campus, will work only through VPN.
To use VPN
- Go to https://vpn.mtu.edu/.
- Log in with Michigan Tech ISO credentials.
- Click on get an MTU address (found under Network Access section).
- Follow subsequent instructions, if any.
- Wait until the browser (or a pop-up browser window)
shows
Status: connected.
Sharing login credentials (username and/or password) with
other and/or unauthorized users is a violation of
Acceptable Use of Information Technologies.
Using this infrastructure in a manner that violates the
above and/or other provisions described in the aforementioned
policy will lead to immediate suspension of account to protect
the integrity of the system and to curtail abuse. To the
extent computer usage is believed to be a violation of
federal, state, or local laws, Michigan Technological
University will turn the matter over to the appropriate
authorities.
Physical access to the computing infrastructure is by
request only and all users will be accompanied by an
authorized staff member of Information Technology Services.
Two Factor Authentication
This optional feature, Two Factor Authentication, expects that the user has a smart phone (Android or iPhone) with Google Authenticator app installed. The procedure is detailed below:
- Install the Google Authenticator (it's free)
using an appropriate link below:
Android | iPhone
- SSH into
rama-login.research.mtu.edu.
- Run
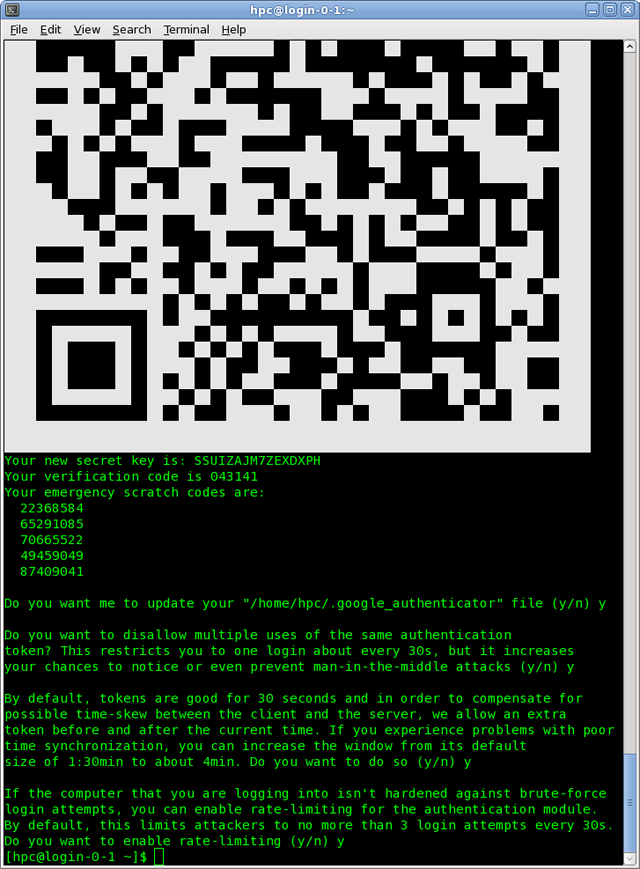
google-authenticator.

- Use Scan Barcode in Google Authenticator app to capture the QR code.
- Make a note of the secret key, verification code
and emergency scratch codes in a secure place.
- Choose
yas an answer for all subsequent questions.
- Inform Information Technology Services so that the administrators can complete the necessary steps.